How Managed Data Protection Can Safeguard Your Company’s Critical Data
How Managed Data Protection Can Safeguard Your Company’s Critical Data
Blog Article
Protect Your Information With Trustworthy Managed Information Security Solutions
In an era where information breaches are significantly common, the importance of robust information security can not be overemphasized. Trustworthy took care of data protection solutions, consisting of Back-up as a Service (BaaS) and Disaster Recovery as a Service (DRaaS), supply a calculated approach to securing sensitive details.
Importance of Information Defense
In today's digital landscape, the relevance of information defense can not be overstated; research studies show that over 60% of tiny businesses that experience a data violation close within 6 months (Managed Data Protection). This alarming figure highlights the essential need for robust data defense techniques, especially for companies that take care of delicate details
Data works as a crucial property for organizations, driving decision-making, customer involvement, and operational effectiveness. A data breach can not just result in considerable economic losses yet additionally harm a company's reputation and erode consumer trust fund. As a result, guarding information should be a top priority for businesses of all dimensions.
Additionally, regulative compliance has ended up being progressively rigid, with laws such as the General Information Security Policy (GDPR) and the California Consumer Privacy Act (CCPA) imposing heavy penalties for non-compliance. Organizations has to apply detailed information security measures to mitigate lawful dangers and support their duty to secure client information.
Sorts Of Managed Solutions
The landscape of information protection remedies has progressed to fulfill the expanding needs for safety and security and conformity. Taken care of services can be classified into numerous kinds, each customized to deal with details organizational needs.
One typical kind is Backup as a Solution (BaaS), which automates the backup process and guarantees data is firmly stored offsite. This technique minimizes the danger of information loss as a result of hardware failures or calamities.
Disaster Healing as a Service (DRaaS) is an additional important solution, supplying companies with the ability to recuperate and restore their entire IT framework swiftly after a disruptive event. This makes certain company continuity and reduces the influence of downtime.
Additionally, Cloud Storage space solutions provide scalable and flexible data storage space options, enabling services to take care of and access their data from anywhere, thus boosting partnership and performance.
Managed Safety And Security Provider (MSS) also play an important role, integrating different protection measures such as risk discovery and feedback, to protect sensitive data from cyber risks.
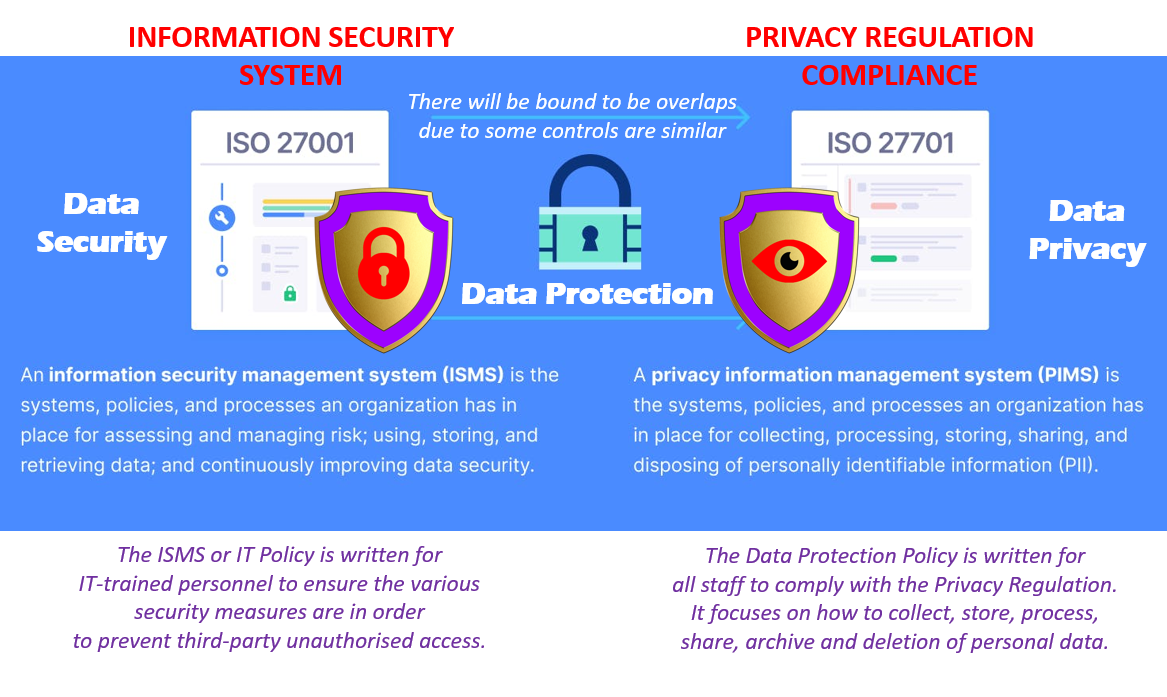
Secret Attributes to Seek
Selecting the appropriate handled information security solution calls for cautious factor to consider of essential functions that align with a company's specific demands. Scalability is crucial; the remedy should fit expanding information volumes without endangering performance. Furthermore, seek extensive insurance coverage that consists of not only back-up and recuperation however additionally data archiving, ensuring all important information is secured.
An additional vital feature is automation. An option that automates back-up procedures reduces the danger of human error and makes sure regular information defense. Additionally, durable protection actions, such as encryption More about the author both in transit and at rest, are important to secure delicate info from unapproved gain access to.
Moreover, the service provider needs to supply adaptable recovery options, consisting of granular healing for specific documents and complete system restores, to reduce downtime during information loss occasions. Tracking and reporting abilities also play a significant duty, as a fantastic read they permit organizations to track the status of back-ups and get informs for any type of issues.
Lastly, think about the service provider's track record and support services - Managed Data Protection. Dependable technical assistance and a tried and tested record in the market can significantly influence the efficiency of the managed information security solution
Benefits of Picking Managed Solutions
Why should organizations consider managed information security services? The primary benefit hinges on the specialized proficiency that these solutions offer. By leveraging a group of specialists devoted to data security, organizations can make sure that their information is protected versus advancing hazards. This proficiency equates right into even more durable protection steps and conformity with sector policies, lowering the danger of information violations.
One more considerable benefit is set you back effectiveness. Taken care of solutions typically lower the need for heavy ahead of time investments in equipment and software, permitting companies to allot resources better. Organizations just pay for the solutions they utilize, which can cause significant cost savings over time.
Furthermore, handled services provide scalability, allowing companies to change their information security strategies in accordance with their development or next altering service needs. This versatility makes certain that their data protection steps stay reliable as their operational landscape evolves.
Actions to Execute Solutions
Implementing handled information protection services involves a series of calculated steps that make certain efficacy and placement with organizational goals. The initial step is carrying out a detailed evaluation of your present information landscape. This consists of identifying essential data assets, reviewing existing security actions, and identifying susceptabilities.
Next, define clear objectives based on the assessment results. Identify what data should be secured, needed recovery time purposes (RTO), and healing factor goals (RPO) This quality will lead service choice.
Following this, engage with handled solution companies (MSPs) to explore potential options. Review their knowledge, solution offerings, and compliance with market criteria. Partnership with stakeholders is critical throughout this phase to guarantee the chosen option fulfills all operational requirements.
Once an option is selected, create a thorough application plan. This plan must detail source allowance, timelines, and training for personnel on the brand-new systems.

Verdict
Finally, the application of reliable managed information security remedies is essential for securing sensitive info in an increasingly electronic landscape. By leveraging services such as Back-up as a Solution (BaaS) and Catastrophe Recuperation as a Solution (DRaaS), organizations can enhance their information security through automation, scalability, and durable security. These actions not just guarantee compliance with regulatory requirements however likewise foster trust among stakeholders and consumers, eventually adding to business resilience and continuity.
In an era where information breaches are progressively widespread, the value of robust information security can not be overstated. Dependable managed data security solutions, consisting of Back-up as a Solution (BaaS) and Catastrophe Healing as a Solution (DRaaS), supply a calculated technique to securing delicate info.Picking the right took care of information defense service needs mindful consideration of essential features that line up with an organization's particular demands. Furthermore, look for extensive protection that includes not just backup and healing however likewise information archiving, ensuring all crucial data is safeguarded.
By leveraging a team of specialists dedicated to data protection, organizations can make sure that their information is safeguarded against progressing threats.
Report this page